Active Directory Federation Services (AD FS) in Windows 2012 R2 have reached the release 3.0. In the long list of new features, an interesting one (dedicated to the world of BYOD) is the workplace join. I have configured workplace join in my lab and used it to authenticate an IPad. The following post explains and shows all the required steps.
Note: the full configuration video is available here http://www.youtube.com/watch?v=vQk2sF-tqf8&list=UUREnpjKgVEWhBxLU9yEDmXQ
Before We Start: Introduction to Workplace Join
Workplace join answer to the need, for users to access company resources from their devices without giving the control on them to the network administrators. However it answers also to the need of the IT staff to keep control on what the device is able to do on the corporate resources. Workplace join enables users to register Windows-based and IOS-based devices for single sign-on and access to corporate data. The aforementioned device ado not join Active Directory, but the workplace join process generates a device object in AD and installs a certificate inside the device. From now on the network administrators are able to use this authentication to allow or remove access to network resources for the device, while users enjoy a single sign-on experience.
To realize my lab, I have used as a starting base this good post from Keith Mayer “Why R2? Step-by-Step: Solve BYOD Challenges with Workplace Join in Windows Server 2012 R2 and Windows 8.1” http://bit.ly/1fc034K
Step by step procedure
First step has been to add the Active Directory Federation Services role to my server Aphrodite (that is also my Domain Controller and Certification Authority).
The configuration of the AD FS role requires a service account, so I created a Group Managed Service Account called FsGmsa with the following cmdlets (adapting the ones used by Keith)
Add-KdsRootKey –EffectiveTime (Get-Date).AddHours(-10)
New-ADServiceAccount FsGmsa -DNSHostName Aphrodite.lync2013.corp -ServicePrincipalNames http/Aphrodite.lync2013.corp
An SSL certificate is required too, so I used my beloved DigiCertUtil to create a CSR. Please note that the Common Name must be the FQDN of the AD FS server, and you need the same name as Subject Alternative Name too. In the SAN names, enterpriseregistration.yourdomain is REQUIRED too.
I have used a command line to submit the request and generate the SSL certificate
certreq -submit -attrib “CertificateTemplate:WebServer” C:UsersAdministrator.WIN-VSNVH4NJGUFDesktopAphrodite_lync2013_corp.txt
Then I have imported (and verified) the aforementioned certificate.
With all the requirements satisfied, I have launched the configuration of the AD FS role
I have defined a standard user, Ipaduser, (I will use it to simulate a real world scenario of a domain user joining his/her IPad to the domain).
I have exported my root CA certificate in a .cer file and copied it on Google Drive (because I need to open it from Safari on the IPad later)
Next step is to initialize the Device Registration Service that, by default, is disabled and stopped. I used the Initialize-ADDeviceRegistrationcmdlet, using, as ServiceAccount, the previously configured Lync2013fsgmsa$
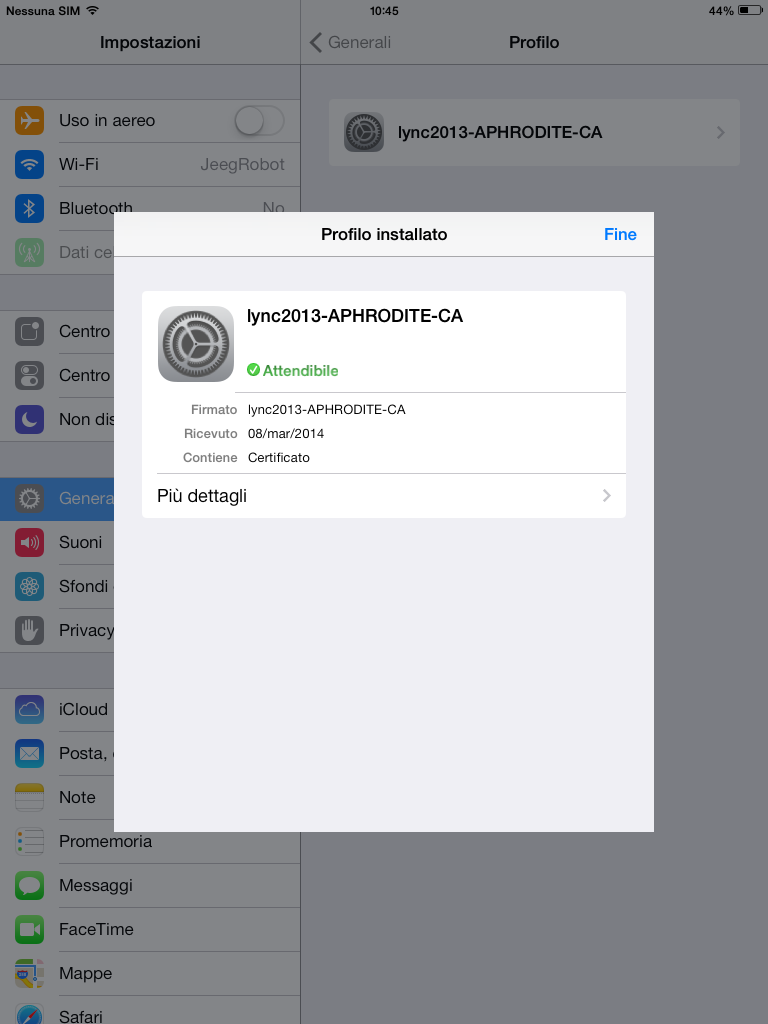
Open the .cer file of the root CA inside Safari and import it as a profile
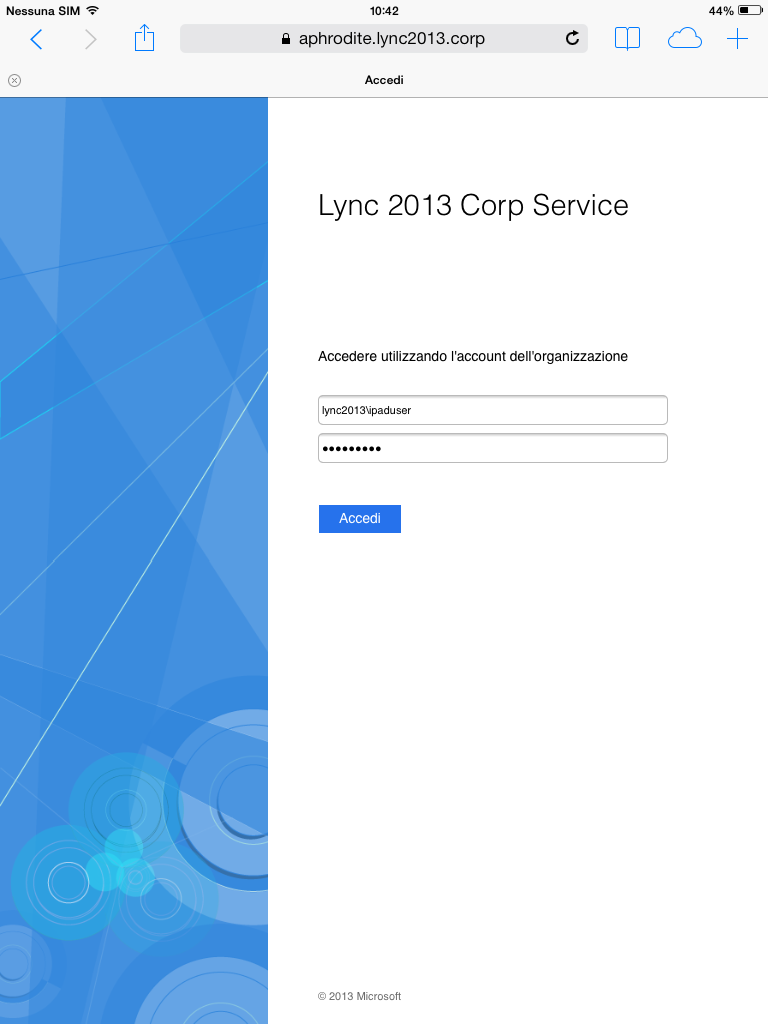
Open the following url https://aphrodite.lync2013.
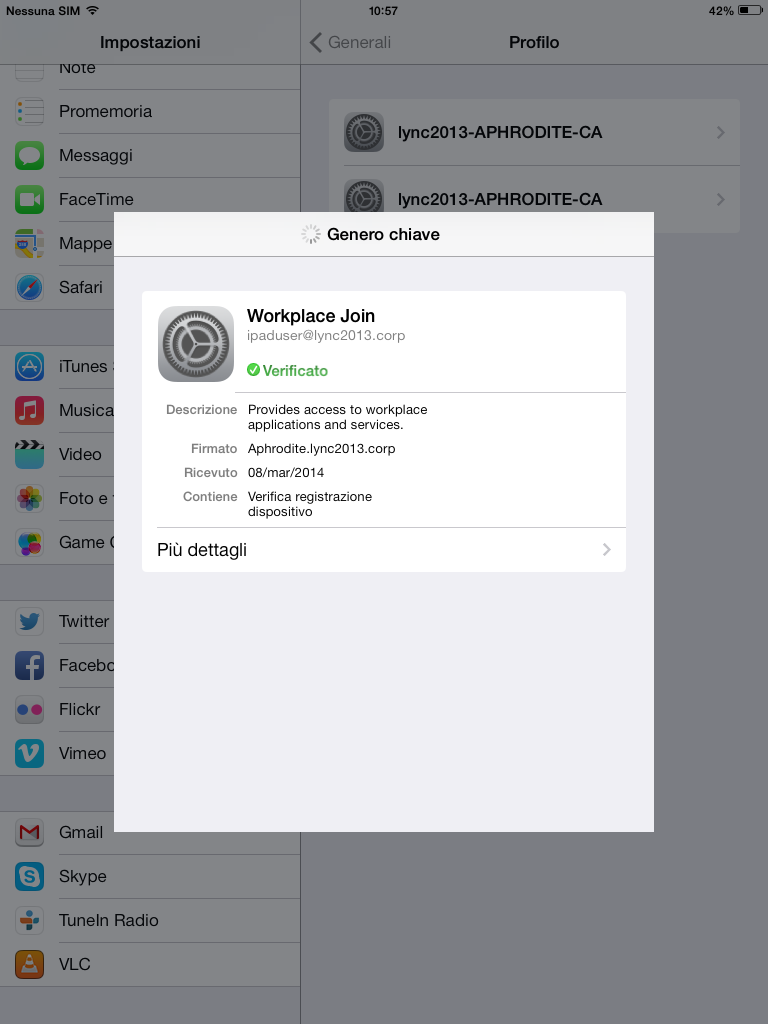
Accept the Workplace Join profile
Then, back to the Aphrodite D.C. I have verified that the device was registered inside A.D.