To make Microsoft 365 administrators’ life easier, it is possible to deploy Defender for Endpoint (Defender) on Android devices registered on Microsoft Endpoint Manager (Intune) as you can see here Deploy Microsoft Defender for Endpoint on Android with Microsoft Endpoint Manager | Microsoft Learn).
However, what is missing is a report that unifies the information stored in Intune and the ones in Defender, so that is possible to understand how many Intune registered devices are still missing the Defender deployment.
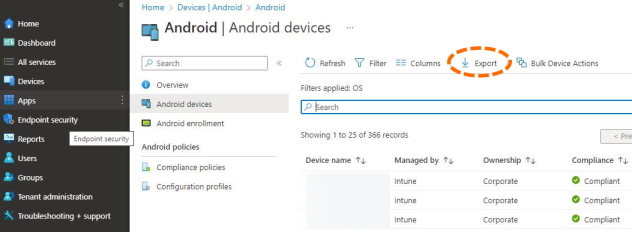
The Intune portal gives you an export of the registered Android devices
The Defender portal gives you an export of all the devices
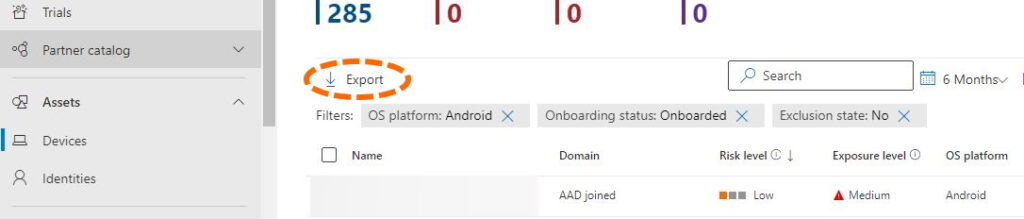
However, the Defender export does not give you any ID number that you can use to match with the Intune export.
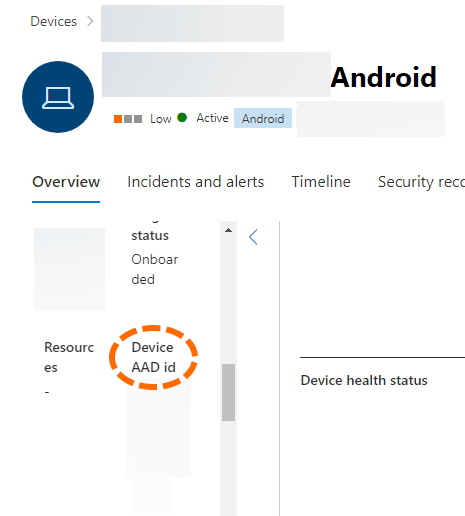
Digging into the Defender reports, at a single device level, you will see a “Device AAD id” value. That could be an useful link to the Intune report that has an “Azure AD Device ID”. However the Defender export does not give you this information
Time for GitHub
Time to use the Microsoft Defender for Endpoint PowerShell module. It is (quoting the GitHub page) “a collection of easy-to-use cmdlets and functions designed to make it easy to interface with the Microsoft Defender for Endpoint API”.
The module requires the registration of an app in the Azure portal and assigning permissions.
When everything is in place, just run the following command (exporting to your favourite folder)
Get-MDATPDevice -All -Verbose | Export-Csv c:\script\DefenderExport.csv
Now you can match the information from Defender (using the aadDeviceId in the DefenderExport.csv file) with the export you did from Intune (using the “Azure AD Device ID” value) using your favourite tool (I was comfortable with Excel)
All the devices in the Intune export not listed in the Defender export require some attention 🙂


