With a recent update, Microsoft has added the capability to use in the Teams app (desktop, mobile and web) both your work account and your personal account (meant to be used to communicate with family and friends).
Whatever is your reaction to this decision there is a practical issue for some companies with strict security requirements. From their point of view access to Teams personal accounts, on the same mobile or desktop used for corporate connection, could impact the security policies.
The next logical step is to disable the access to Teams personal accounts on the devices used for work. A similar issue (and solution) can be used to limit access to unapproved Office 365 tenants. Surprisingly, the above control is not something that you can do using a Teams policy.
Teams Free account
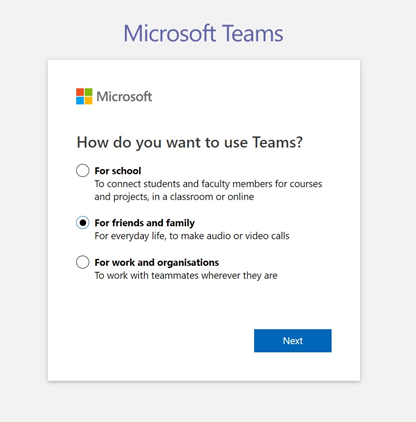
Creating a free account in Teams requires just a few steps (see images below) and you can use an existing email address
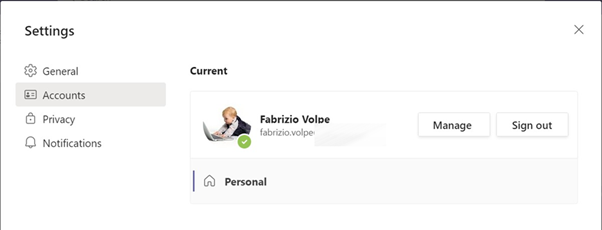
The new account will be shown as “personal
Desktop App Experience:
Now, inside the desktop app, you are able to add your personal account
After that, it is easy to switch between the two accounts
The personal account will open as an additional window
Blocking Undesired Teams Logins in Windows 10
A post from Microsoft explains (also) how to “Restrict sign in to Teams” https://docs.microsoft.com/en-us/microsoftteams/sign-in-teams#how-to-restrict-sign-in-on-desktop-devices
A paragraph is dedicated to mobile devices and another one to Windows 10 access. For this post I will focus on how to restrict sign-in on desktop devices / Windows 10.
The policies can be set using
- Device Management solutions such as MDM (Mobile Device Management)
- GPO (Group Policy Object)
To use the GPOs, you should install the “Administrative Template files (ADMX/ADML) and Office Customization Tool for Microsoft 365 Apps for enterprise, Office 2019, and Office 2016”
https://www.microsoft.com/en-us/download/details.aspx?id=49030
Note: Supported Operating System for the DC is Windows Server 2016 and Windows Server 2019
As an alternative, it is possible to apply the required changes to the Windows Registry (I will explain this one after the GPO based approach)
Blocking Logins Using GPOs
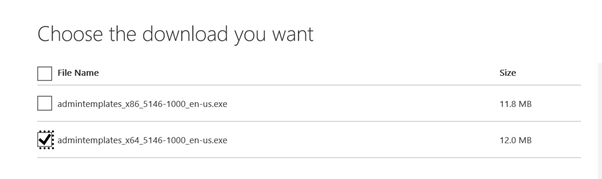
To add the required Administrative Templates, download the correct version (X86 or x64) and decompress the files in a folder
You are able to copy the required files into a Central Store ( see the Microsoft document https://docs.microsoft.com/en-us/troubleshoot/windows-client/group-policy/create-and-manage-central-store) and finally use them inside a GPO.
In my test the Central Store was \\test2019.corp\sysvol\Test2019.corp\Policies\PolicyDefinitions
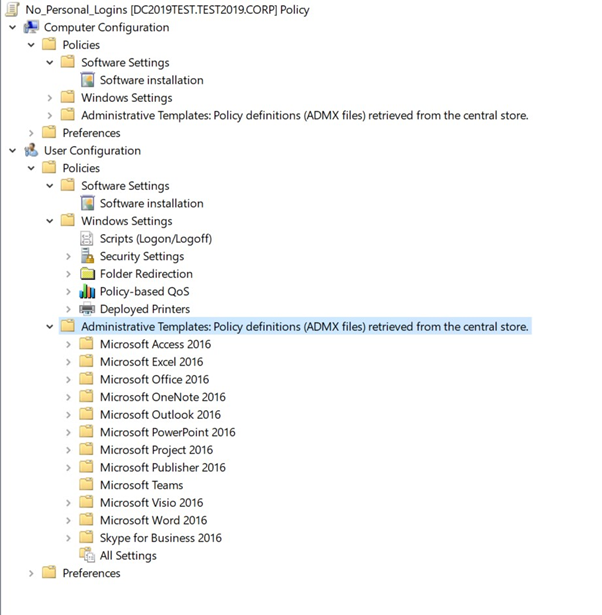
Using Group Policy Management I have created a policy called “No_Personal_Logins“
The imported ADMX files are shown in the GPO
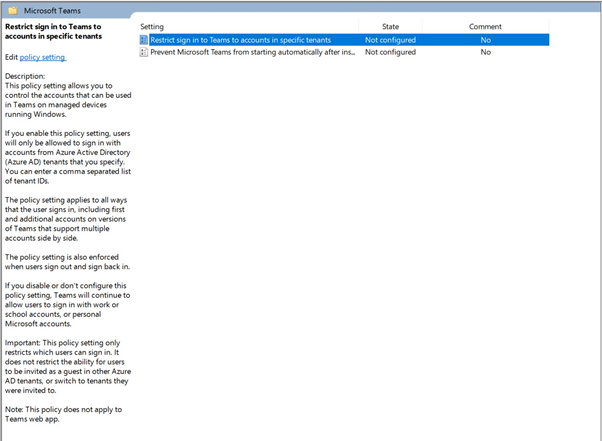
Under User Configuration – Administrative Template Policy Definitions – Microsoft Teams we have a parameter called “Restrict Teams Signin to Accounts in Specific tenants”
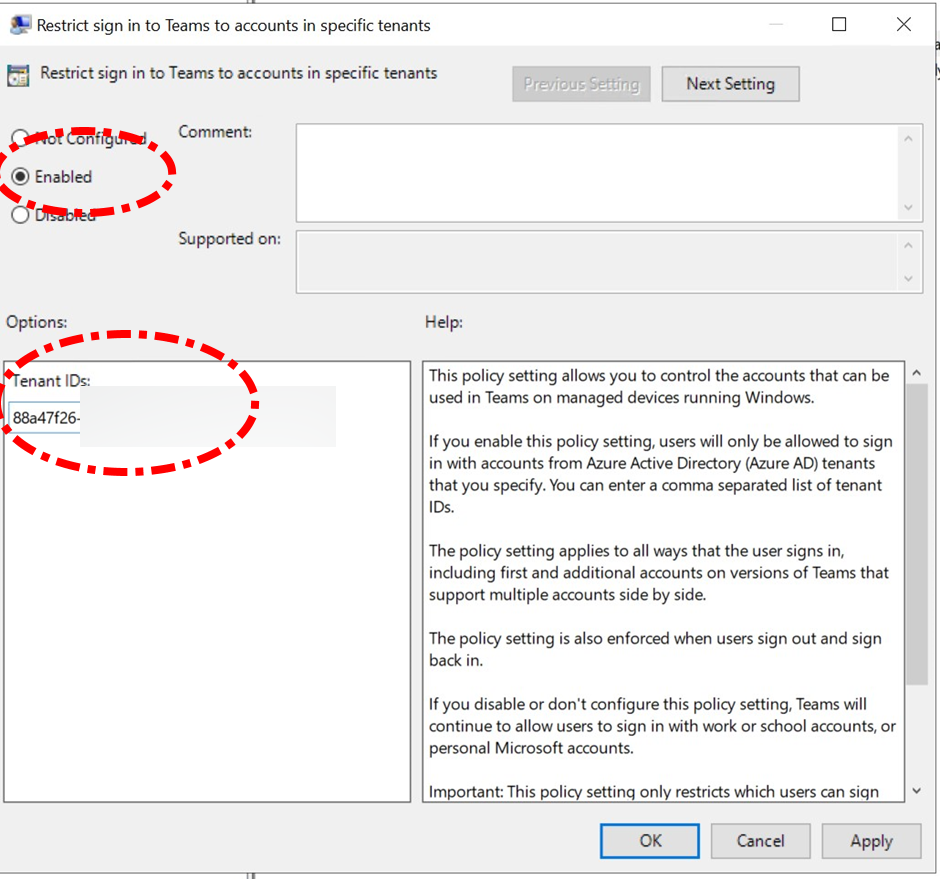
The parameter is set to Enable, the list of the authorized tenant uses the Tenant IDs (if you want to know it from the domain FQDN I suggest using https://www.whatismytenantid.com/ ). Each Tenant ID must be separated using comma
Windows 10 User Experience
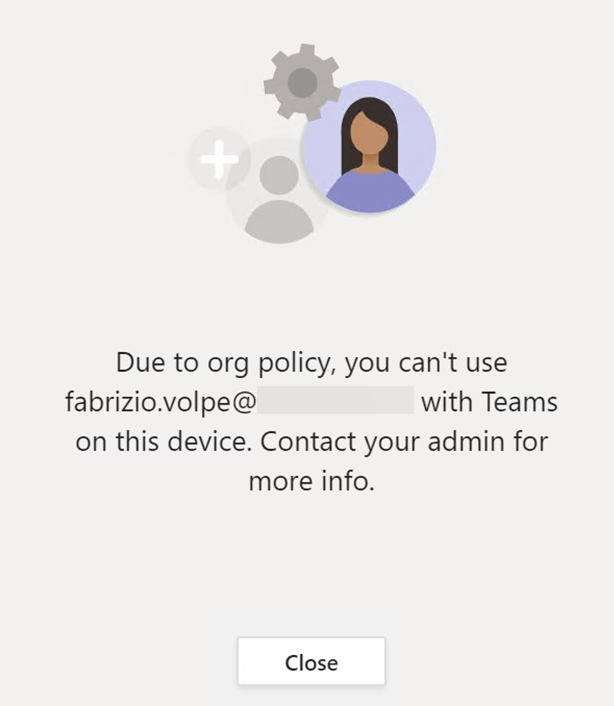
If you try to switch to an unauthorized account, now, you have the message below
Similar, if you try to start Teams with the unauthorized account
What the GPO Does – Manual Approach in REGEDIT
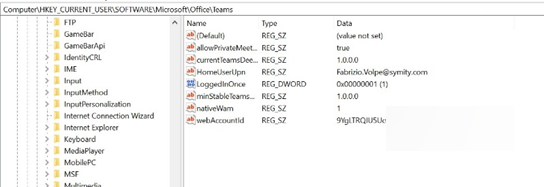
As you can see in the image below, a new Registry Key is created
You have the same result modifying the registry (as for the Microsoft document mentioned before)
Value Name: RestrictTeamsSignInToAccountsFromTenantList
Value Type: String
Value Data: Tenant ID, or comma-separated list of Tenant IDs
Path: use one of the following
Computer\HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\Cloud\Office\16.0\Teams Computer\HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\Office\16.0\Teams Computer\HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Teams